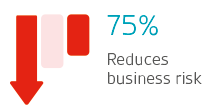
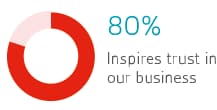
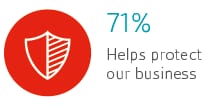
Learn how to manage information security by training with our experts
Our ISO/IEC 27001 training courses follow a structure to help you familiarize yourself with the standard, understand how to implement an ISMS, and how to audit it.
Get ISO 27001:2022 training with BSI
Discover how BSI's ISO/IEC27001:2022 training courses can help you understand, implement and audit the changes effectively, from revised Annex A controls to four new security categories. In this 4 minutes video, we will provide an overview of the new available ISO/IEC 27001:2022 training courses and the difference.